Keeping your code safe: Secure Processors
Performing your banking with an unsecured connection, or surfing the web without a anti-virus is dangerous to say the best. Your data may become compromised which of course could serious ruin your day. These problems extend to the hardware level as well. In such things as your microwave, their is software running on the hardware to control it. It would be possible to extract this software code given the right tools. Stealing kitchen appliance code is not a particular threat obviously. However, there ARE applications where the software running on a set of hardware IS very important, more so often then the hardware itself. Take for example the battlefield management software on a tank, or the flight control system on a F-22A Raptor. This is not something you want someone to be able to recover.
Several companies make what are called ‘Secure Processors.’ These are processors designed to keep the code on them VERY secure. Above is one from Maxim, tamper with it, and the SRAM is auto erased to all 0’s rendering the code useless. It has encrypted data buses, on-board AES encryption, random key generators, the works.
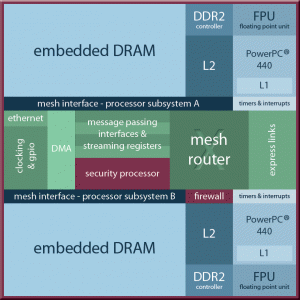
A Company called CPU Tech has a processor called the CPU872, which is now available for commercial use (previous designs have been DoD only). Programs are securely booted from encrypted flash and decrypted onto on-chip embedded DRAM, and neither cleartext nor the decryption key is ever accessible, according to CPU Tech. In a multi-processor system, all I/O communication between CPU872 devices is also secured, according to the firm. This processor includes 8MB of onboard DRAM, as well as a pair of 800MHz PowerPC 440 cores. The security however doesn’t start at the chip; CPU Tech only uses ‘Trusted Foundaries’ in the manufacture of their parts, to ensure malicious hardware is not added to the part during fabbing.